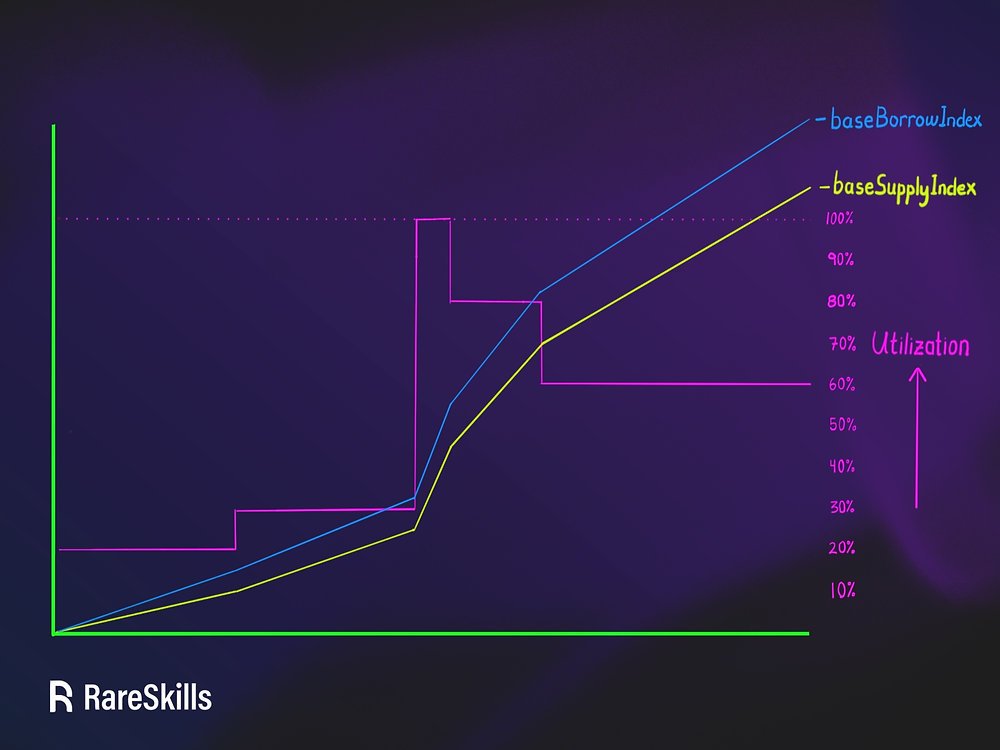
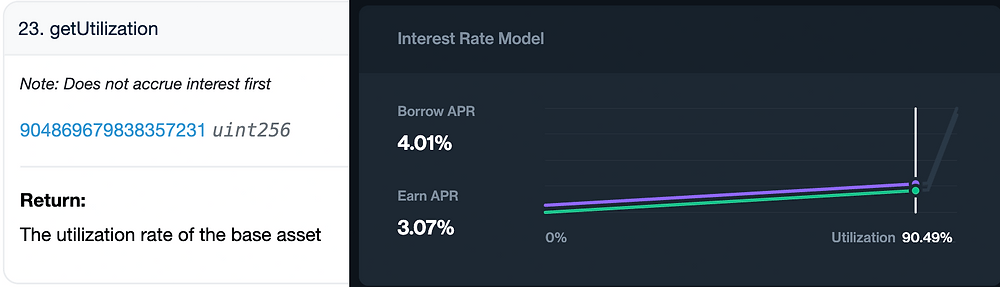
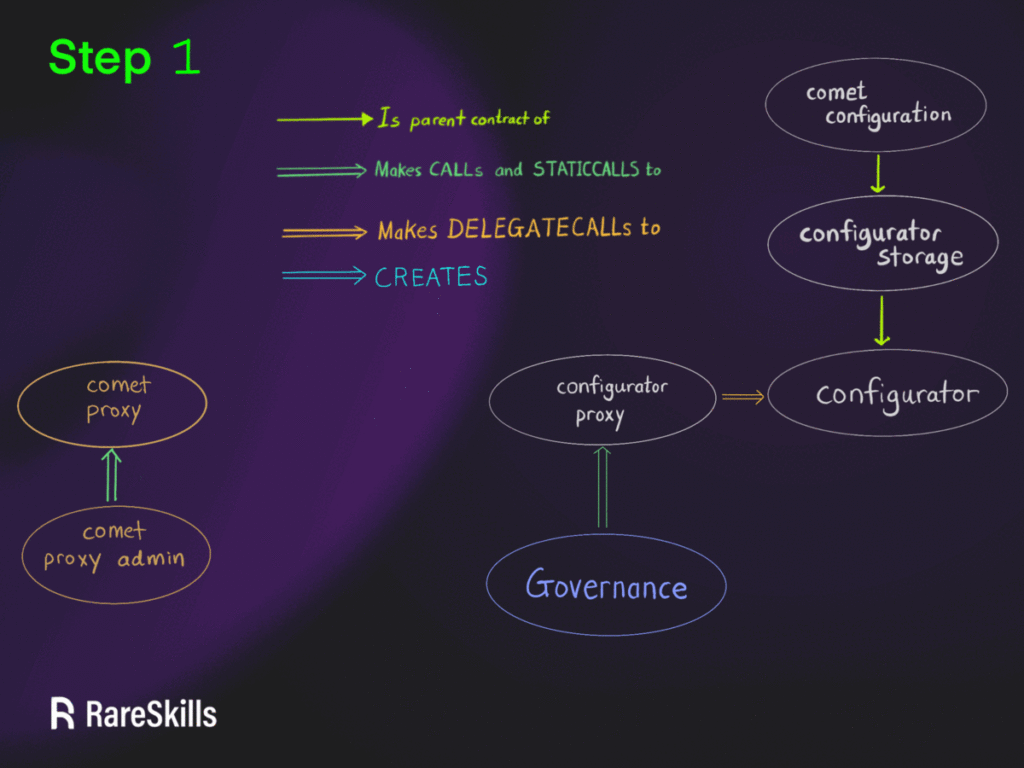
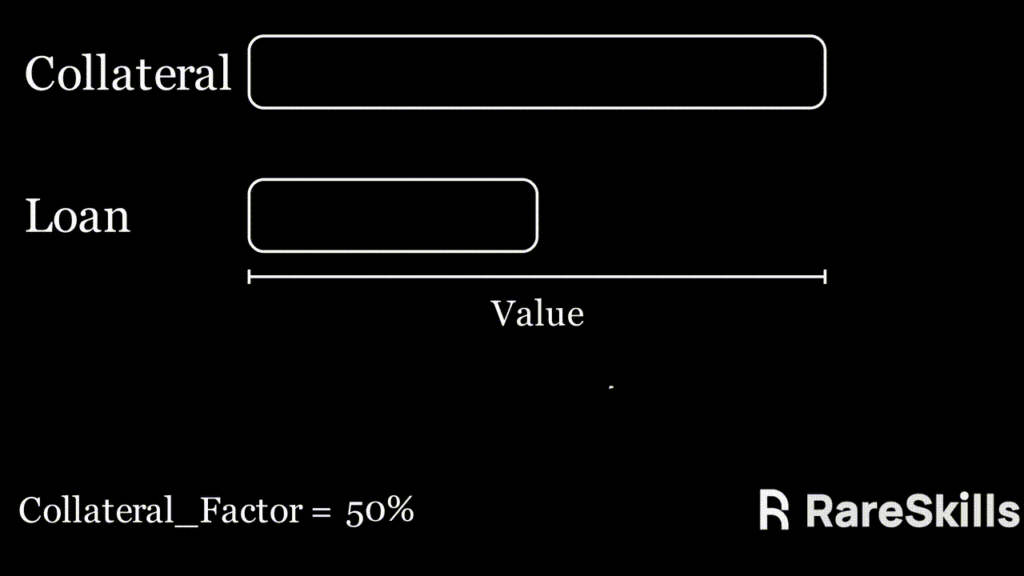
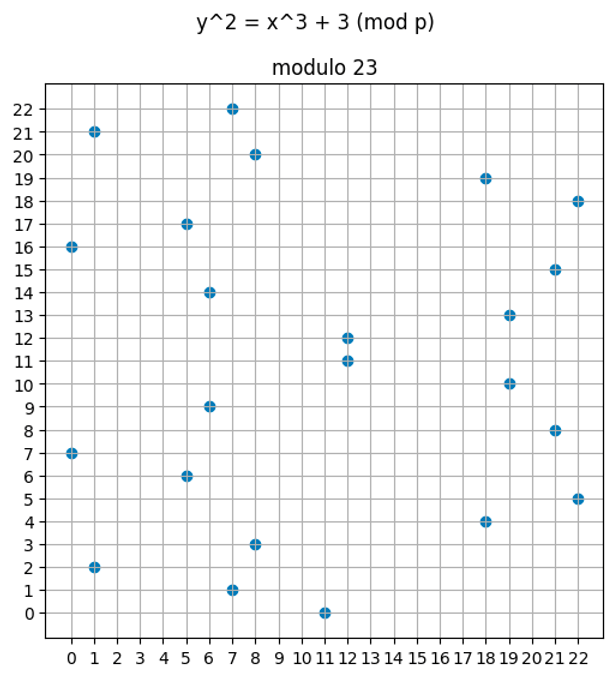
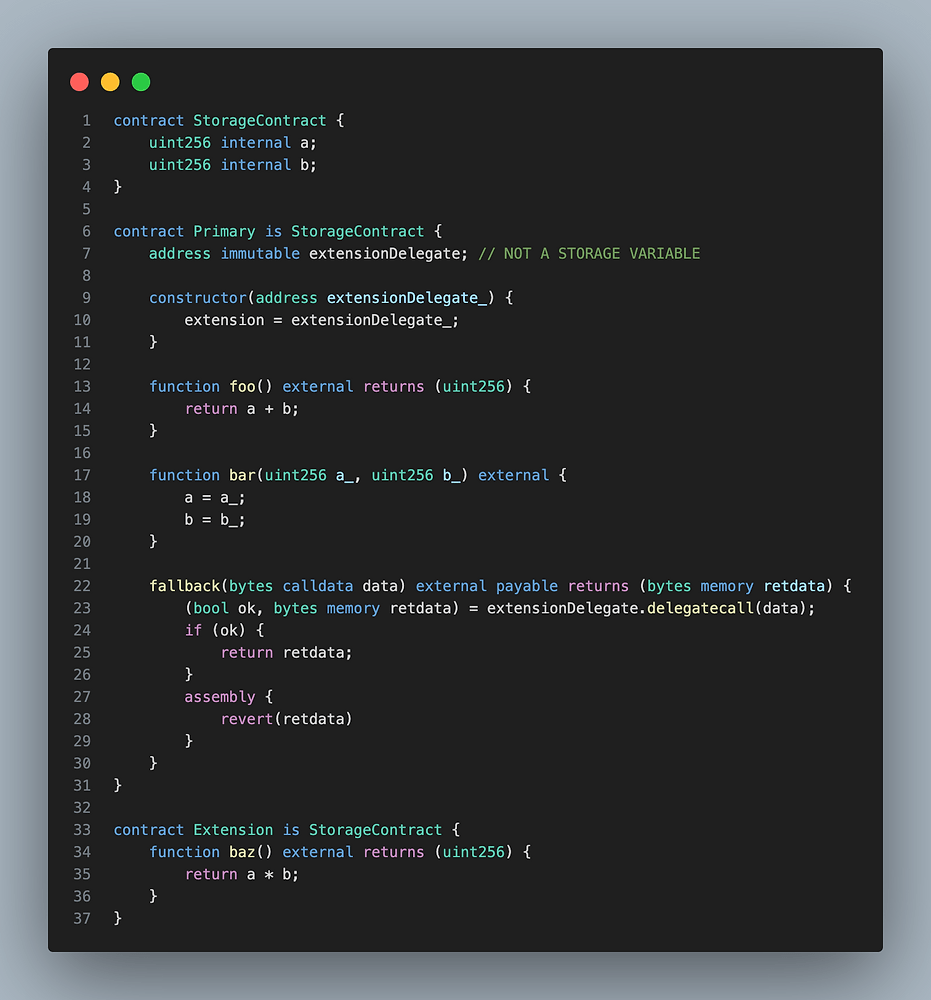
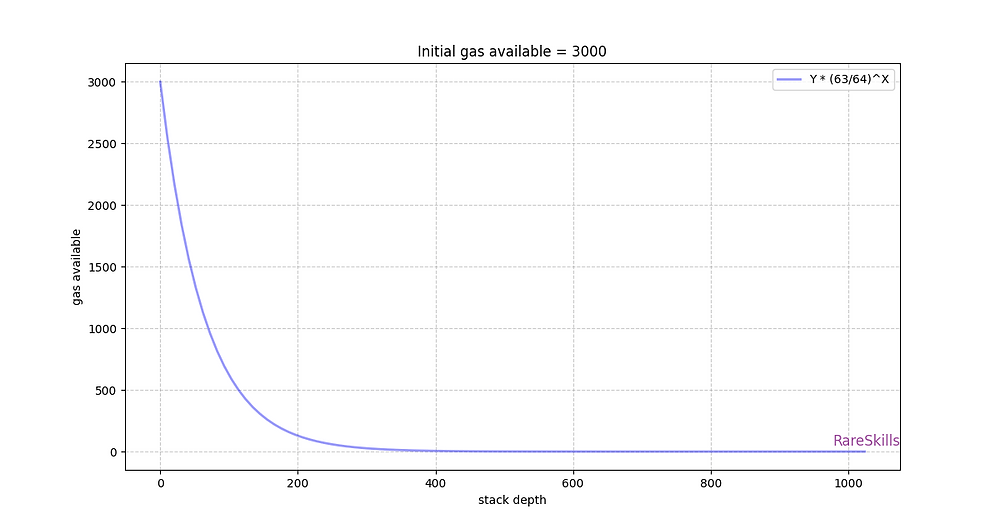
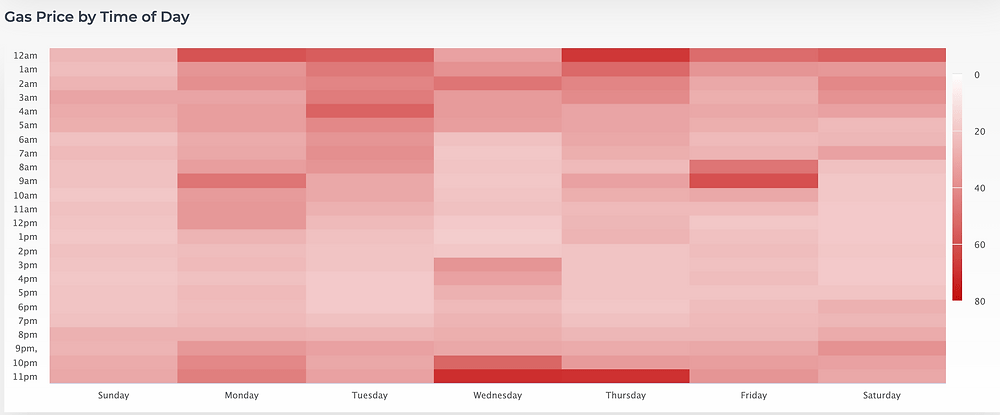
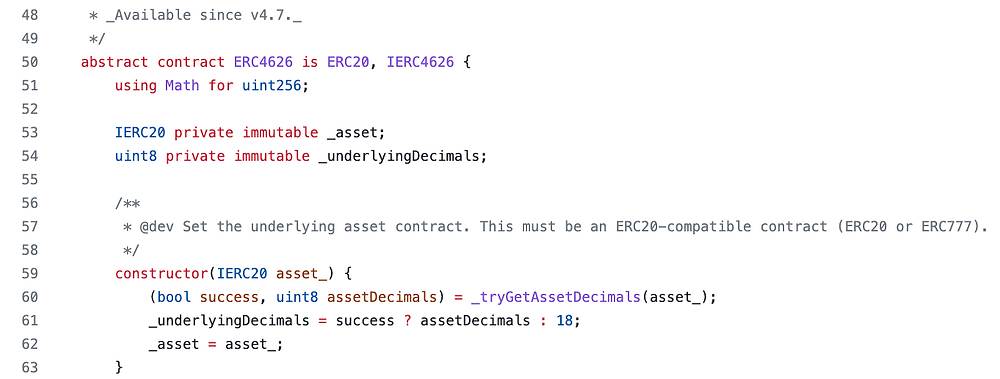
Multiplicative Subgroups and Primitive Elements
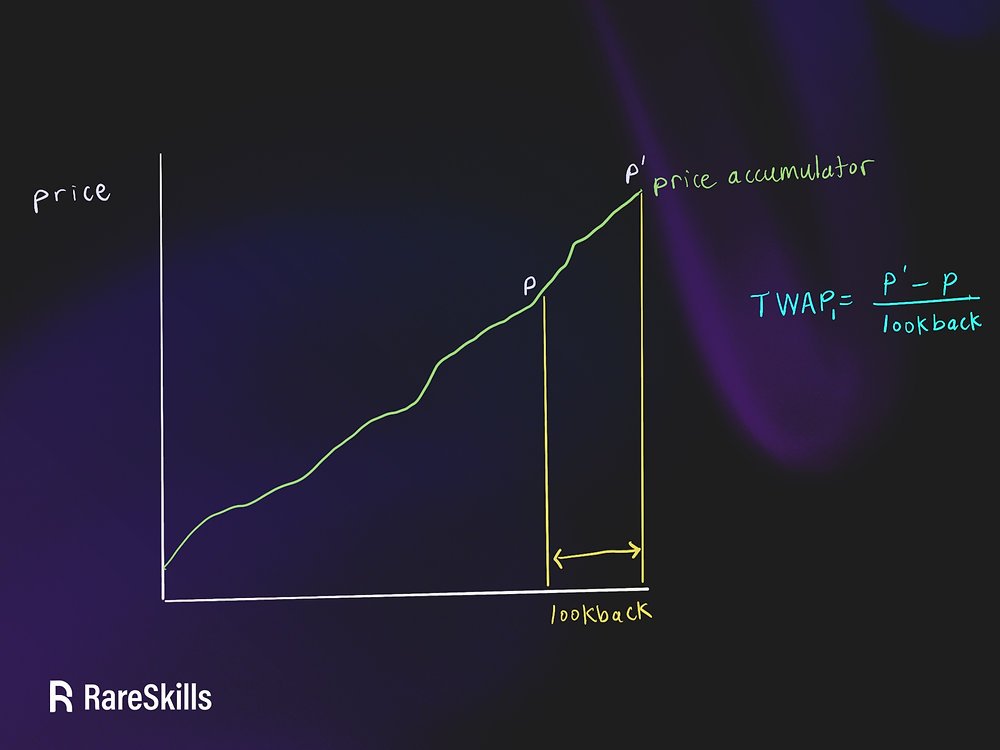
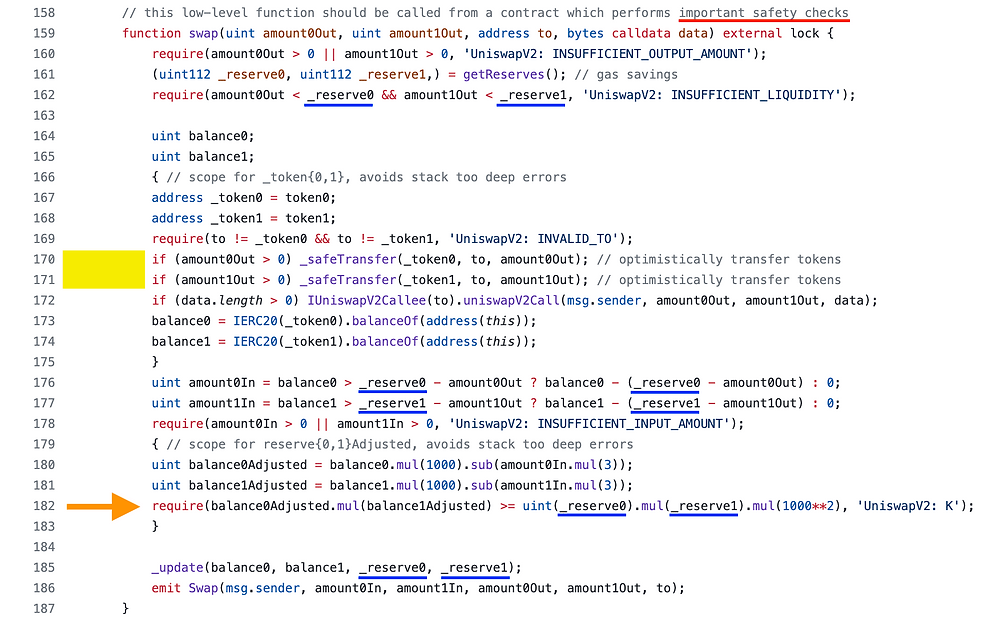
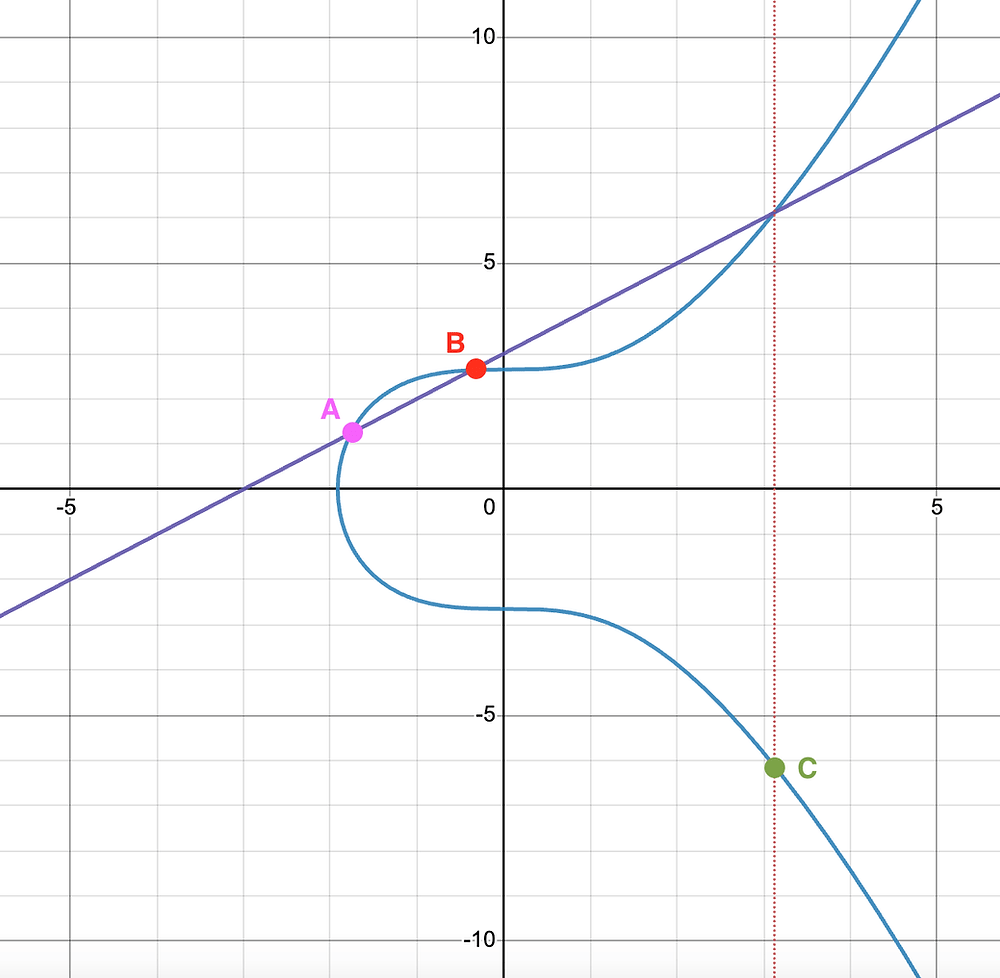
Multiplicative Subgroups and Primitive Elements Introduction This chapter continues our study of group theory by exploring subgroups and generators. The concept of a primitive element will be introduced at the end. We assume you are already familiar with the definition of a group. If you need a refresher, check out this article. To build intuition, […]
















![#[derive(Accounts)] in Anchor: different kinds of accounts](https://www.rareskills.io/wp-content/uploads/2024/08/935a00_05694389f65848dfb3dee8af7aa05874mv2-1024x576.jpg)